Download PDF
What is SOC 2 compliance?
SOC 2 (System and Organization Controls 2) is a compliance framework developed by the American Institute of Certified Public Accountants (AICPA). It is designed to assess how well a company manages customer data based on a set of five key Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
SOC 2 compliance is crucial for organizations handling sensitive customer information, SaaS companies, cloud service providers, and financial institutions. It assures clients and partners that their data is protected against breaches, unauthorized access, and operational failures.
SOC 2 Trust Services Criteria
SOC 2 compliance is built around five core Trust Services Criteria (TSC) that define key areas of security and data protection:
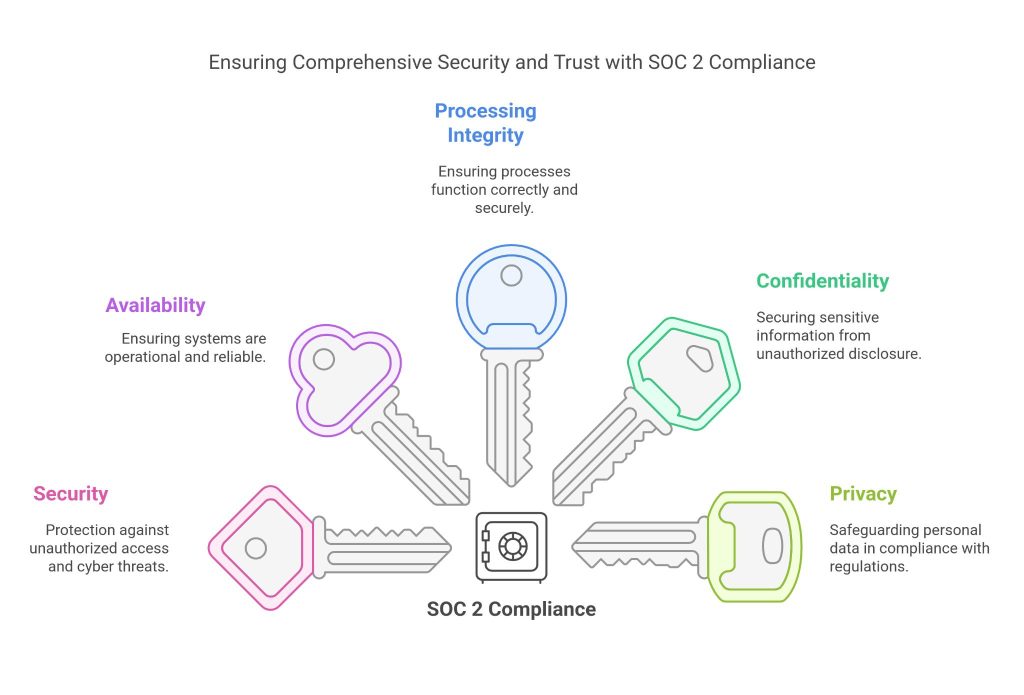
- Security: Protection against unauthorized access, breaches, and cyber threats.
- Availability: Ensuring systems and services are operational and reliable for customers.
- Processing Integrity: Ensuring that system processes function correctly, securely, and without errors.
- Confidentiality: Securing sensitive business and customer information from unauthorized disclosure.
- Privacy: Safeguarding the personal data of customers and users in compliance with regulatory requirements.
Sahl helps organizations continuously monitor, enforce, and validate these principles, ensuring a strong security posture and SOC 2 readiness.
Automate SOC 2 Compliance and Reduce Effort
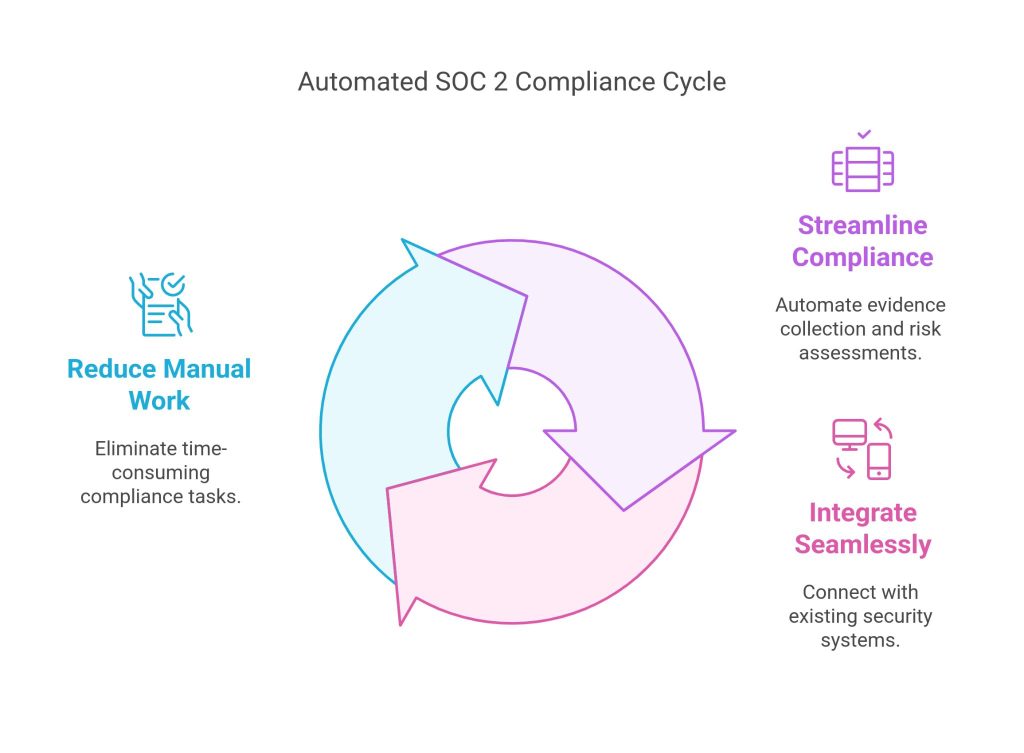
Achieving and maintaining SOC 2 compliance requires continuous monitoring, evidence collection, and risk assessment. Sahl automates these processes, enabling businesses to:Streamline Compliance – Automate evidence collection, risk assessments, and security monitoring to ensure continuous SOC 2 readiness.
Integrate Seamlessly – Connect with your existing security stack to enforce SOC 2 controls effortlessly.
Reduce Manual Work – Eliminate time-consuming compliance tasks with automated tracking of Trust Services Criteria (TSC).
Streamline compliance, Integrate seamlessly, Reduce manual work

SOC 2 Type 2
Download this checklist to assess the operating effectiveness of your controls over a period of time, demonstrating that your controls are operating as designed and achieving the intended security objectives.
Stronger Security, Seamless Compliance
With real-time security monitoring, automated compliance checks, and expert-guided remediation, Sahl helps businesses proactively manage risks and avoid security gaps.
Our platform ensures compliance with SOC 2 Type I (point-in-time audit) and SOC 2 Type II (ongoing compliance tracking) without disrupting business operations.
SOC 2 Type I vs. SOC 2 Type II Audits
SOC 2 Type I evaluates whether an organization has the necessary security controls in place at a specific point in time, focusing on their design and implementation. It is a quicker process and serves as an initial validation of security measures.
SOC 2 Type II, however, assesses how effectively these controls operate over a period of time, usually 3 to 12 months. This audit provides a more in-depth evaluation of ongoing compliance, making it a stronger assurance of security and reliability.
With automated risk detection and audit-ready reporting, Sahl simplifies compliance for businesses of all sizes.


