Navigating today’s complex web of international privacy and cybersecurity laws is no easy task. From the U.S.-based NIST framework to Saudi Arabia’s PDPL, businesses face mounting pressure to comply with multiple, overlapping regulations. That’s where an AI-powered unified compliance dashboard becomes essential — consolidating global frameworks into a single platform that simplifies risk management, speeds up audits, and turns compliance into a strategic advantage.
How do businesses stay ahead? The centralization of power technology, and analytics hold the key to the solution.
A system that unifies several legal demands into a single, intuitive user interface is the unified compliance dashboard. Businesses are obtaining immediate awareness, actionable knowledge, and flexible workflows by incorporating AI into risk and compliance management. This turns legal compliance from a burden into a competitive advantage.
With an emphasis on machine learning, expansion, and cross-framework position, we’ll examine in this article how creating a unified compliance dashboard may streamline your company’s transition from paradigms like NIST to PDPL.
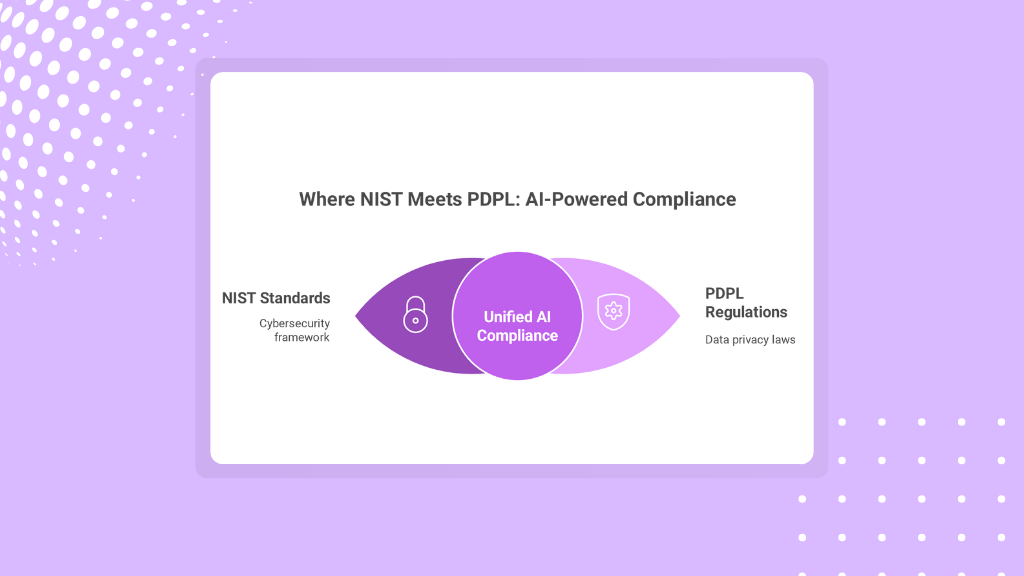
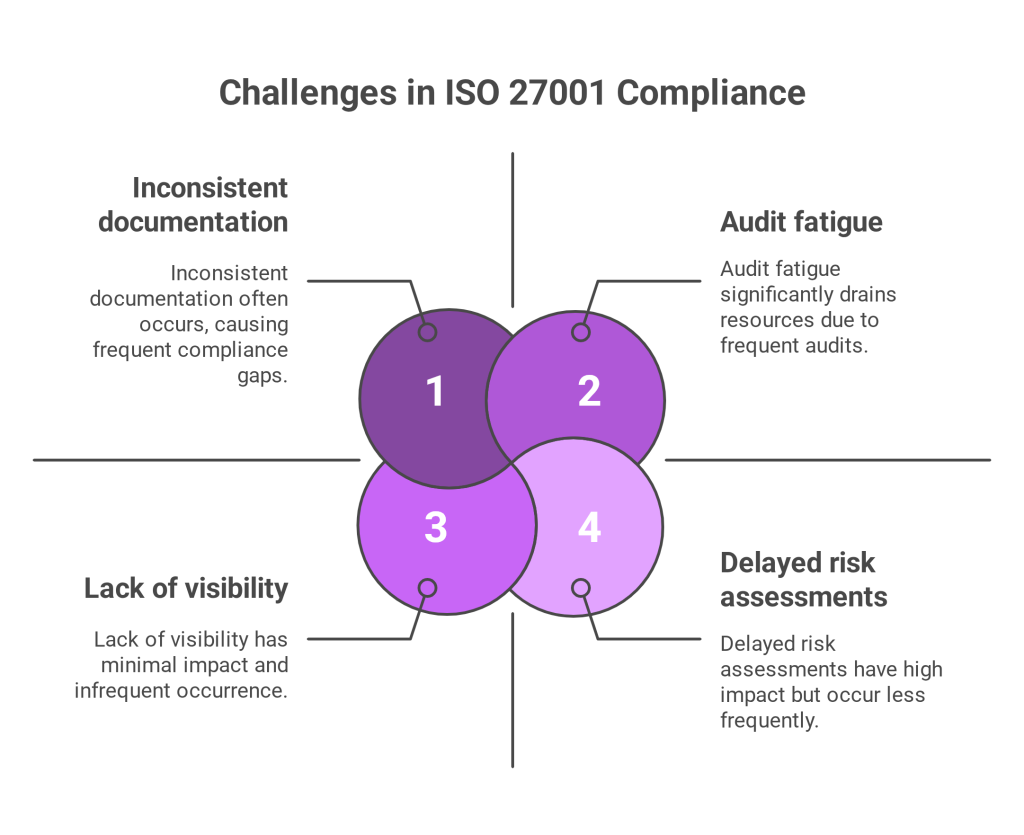
The Complexity of Compliance: NIST vs. PDPL
Every jurisdiction has its own approach to data protection and security. NIST, commonly adopted by US based organizations, offers a detailed framework for identifying, detecting, responding to, and recovering from cyber threats. Meanwhile, Saudi Arabia’s PDPL enforces strict privacy principles such as data minimization, clear consent, and cross border data restrictions.
Trying to handle each of these structures independently leads to inefficiency, duplication of effort, and a higher risk of disobedience. In order to integrate processes across regulatory boundaries, businesses need an administrative solution, with one safety dashboard.
What Is an AI-Powered Unified Compliance Dashboard?
A computerized control center that unifies several security, privacy, and threat compliance requirements into just one user interface is called a unified compliance dashboard. The control panel tracks and analyzes generic control systems, statistics, and paperwork in one location rather than maintaining NIST, PDPL, ISO 27001, and GDPR independently.
The benefits include:
- Centralised oversight of compliance across frameworks
- Real time alerts for non compliant activity
- Automated reporting and documentation
- Role based access and task management
The dashboard becomes your single source of truth, simplifying decision making and proving compliance with minimal manual effort.
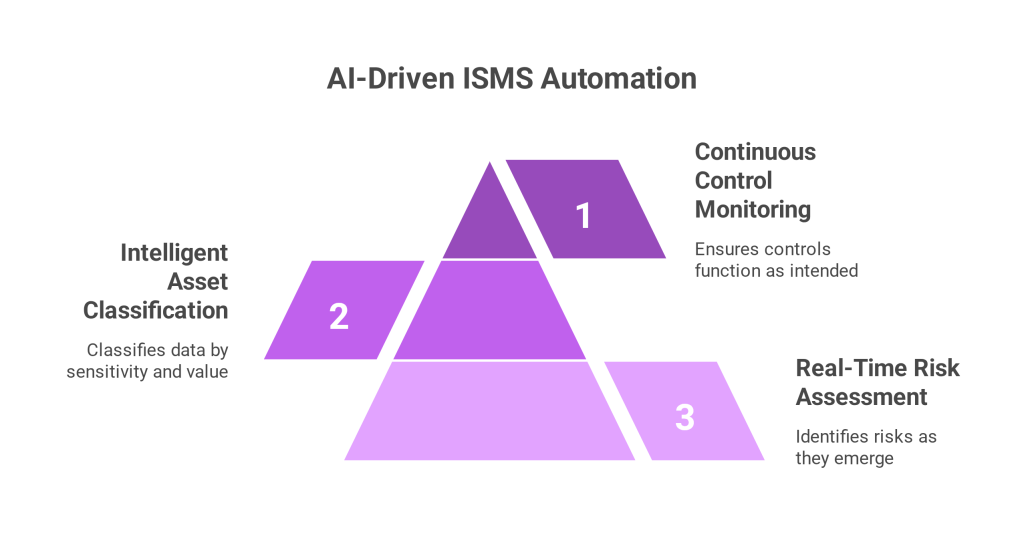
How AI Enhances Risk & Compliance Management
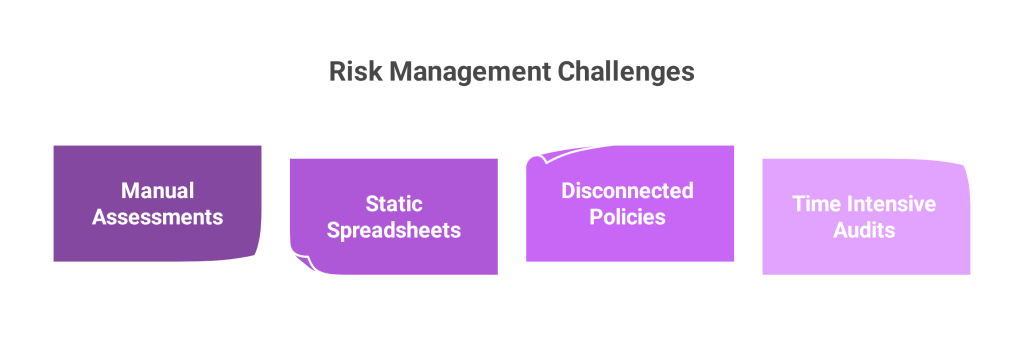
Traditional compliance programs rely heavily on human monitoring, paper based checklists, and fragmented documentation. These methods can’t scale or adapt quickly.
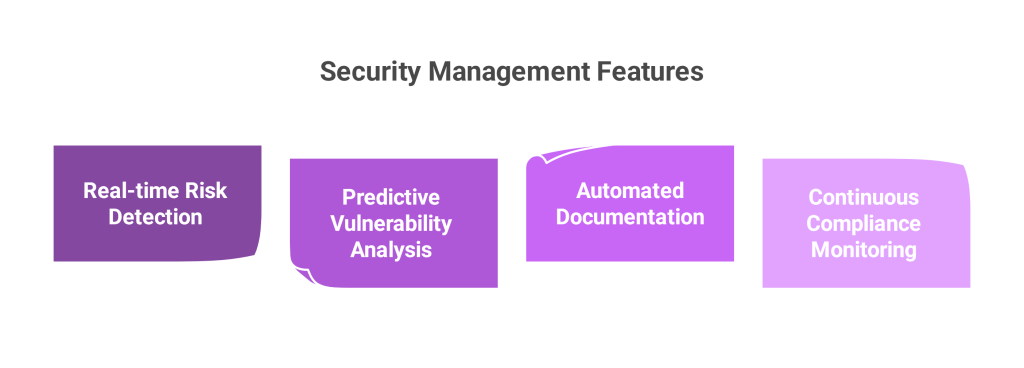
Integrating AI in risk and compliance management revolutionizes how teams interact with compliance data. AI enables:
- Predictive analytics to forecast risks
- Natural language processing for interpreting regulation texts
- Pattern recognition to flag anomalies or gaps
- Automated control mapping across frameworks
Combined with a privacy compliance dashboard, AI helps organizations stay one step ahead of regulatory changes.
NIST Compliance Automation: The Starting Point
For many organizations, NIST is the foundation of cybersecurity and risk governance. It provides detailed controls around access management, incident response, and continuous monitoring.
Using a unified compliance dashboard, AI can automatically:
- Cross reference NIST controls with other frameworks like PDPL or GDPR
- Track risk posture changes over time
- Trigger real time alerts for non compliance
- Recommend remediation steps using past patterns
This is what makes NIST compliance automation so powerful; it ensures security compliance is dynamic, data driven, and consistent across your ecosystem.
Mapping Compliance Across NIST and PDPL
While NIST focuses heavily on security controls, PDPL leans toward privacy rights, consent, and lawful processing. Despite their differences, there are overlaps in principles like data integrity, user access, and incident reporting.
Compliance mapping NIST PDPL allows organisations to:
- Identify shared requirements between frameworks
- Reuse documentation and evidence across audits
- Avoid duplicated efforts in policy enforcement
- Spot contradictions and address them proactively
AI driven mapping tools built into a unified compliance dashboard make this process much faster and more accurate than manual cross referencing.
Real Time Monitoring and Adaptive Governance
One of the major advantages of a unified compliance dashboard is its ability to provide real time monitoring. Whether you’re preparing for a NIST audit or updating your data consent workflows under PDPL, the dashboard gives you:
- Live compliance scores and health indicators
- Custom alerts for high risk activities
- AI powered recommendations for policy adjustments
- Illustration of regulatory tensions and overlaps
Compliance thus turns into an evolving method that adjusts to changing conditions in your business or the regulatory landscape.
The Power of Automation in Privacy Compliance Dashboards
A privacy compliance dashboard ensures that privacy regulations like PDPL, GDPR, and CCPA are not just tracked but operationalized.
Key features powered by AI include:
- Consent tracking and lifecycle management
- Data subject request automation
- Cross border data flow assessments
- Automatic policy enforcement and logging
The result? Compliance that is proactive, verifiable, and consistent backed by real time AI insights that scale with your organisation.
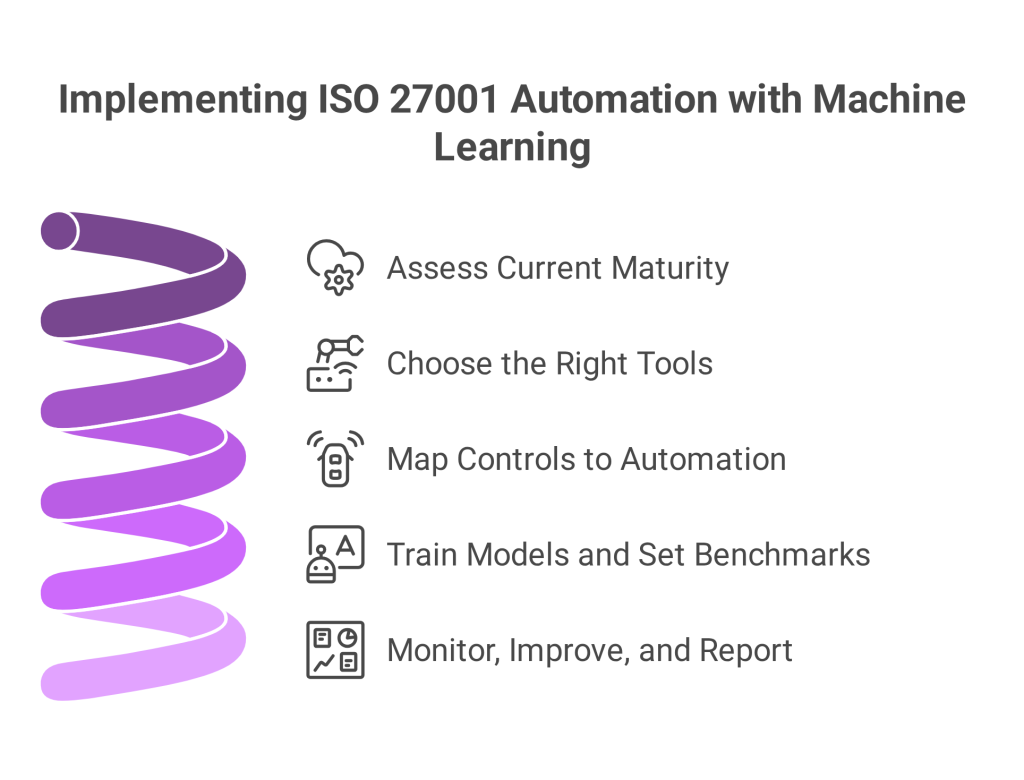
Unified Compliance Dashboard: Implementation Roadmap
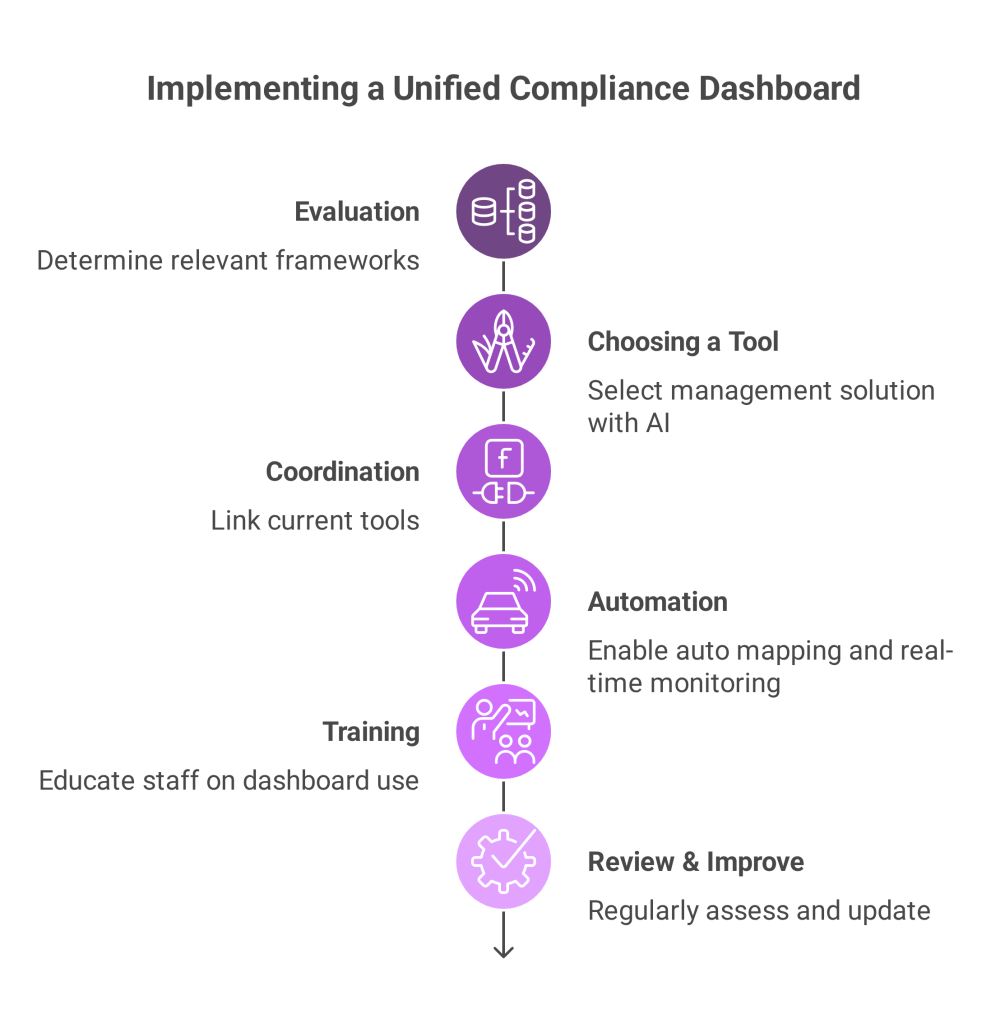
Adopting a unified dashboard doesn’t happen overnight. Here’s a simplified roadmap:
- Evaluation: Determine which frameworks (NIST, PDPL, ISO 27001, etc.) are relevant.
- Choosing a Tool: Select a management solution with robust artificial intelligence features.
- Coordination: Link current tools (cloud providers, GRC, HR, and ITSM).
- Automation: Enable auto mapping of controls and real time monitoring
- Training: Educate staff on dashboard use and AI features
- Review & Improve: Regularly assess dashboard output and update as regulations evolve
By following these steps, teams can transition from reactive compliance to a fully integrated, risk informed model.
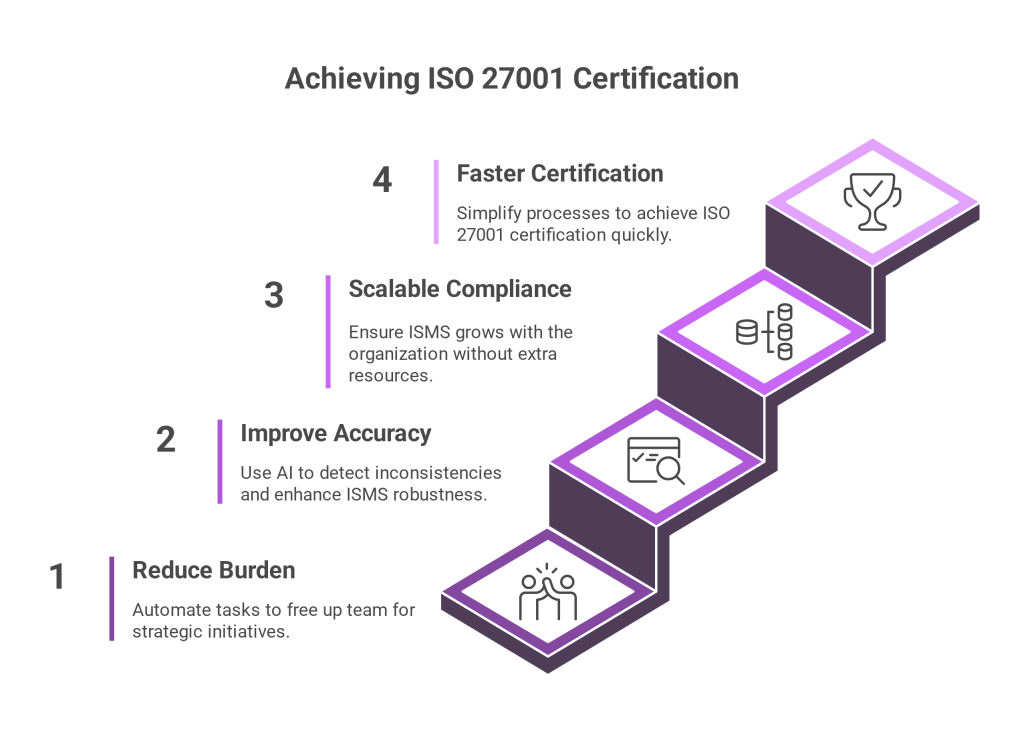
From Compliance to Competitive Edge
Gaining the trust of stakeholders and enhancing operational resilience are two more goals of a unified compliance dashboard beyond merely fulfilling legal requirements. Benefits spread throughout the entire company, whether it’s meeting audit requirements, lowering breach risks, or speeding up product introductions.
AI and compliance dashboards work together to help businesses that operate internationally or in regulated sectors adjust more quickly, be more transparent, and save a lot of money.
Conclusion
Businesses can now not afford to ignore safety as an extra in light of the growing number of regulations and requirements. Even the most disjointed compliance systems can benefit from technology, clarity, and structure provided by a unified compliance dashboard driven by AI. Benefits flow across the entire organization, whether it’s accelerating product launches, reducing breach risks, or satisfying audit needs.
Such dashboards enable confidentiality and safety teams to work more efficiently rather than more laboriously, from NIST compliance automation to NIST PDPL compliance mapping. And that’s a benefit worth investing in in an economy where honesty and confidence are essential distinctions for businesses.
What is a unified compliance dashboard?
It’s a centralized platform that tracks, manages, and reports on multiple regulatory frameworks in one interface, powered by AI.
How does AI improve risk and compliance management?
AI enables predictive analytics, real time alerts, and control mapping across frameworks, helping teams act quickly and accurately.
Can I use one dashboard for both NIST and PDPL?
Yes. A well designed unified compliance dashboard can map and manage both frameworks simultaneously, avoiding duplicate work.
What are the benefits of compliance mapping between NIST and PDPL?
Compliance mapping allows organizations to align overlapping controls, reduce duplication of effort, and streamline reporting across different frameworks. It ensures consistency while saving time and resources during audits.
Is this solution scalable for SMEs?
Absolutely. Many AI powered dashboards are designed to grow with your business, from startup to enterprise.
How long does it take to implement a unified compliance dashboard?
Depending on your tools and frameworks, initial implementation can take a few weeks to a few months.
How does a privacy compliance dashboard handle data subject requests?
AI-powered dashboards can automate the intake, verification, and fulfilment of data subject requests (DSRs), such as access, deletion, or correction, while logging each step for audit readiness and accountability.