SOC 2

What is SOC 2 Compliance?
SOC 2 Compliance helps organizations meet the standards set by the American Institute of Certified Public Accountants (AICPA). It measures how well a business manages customer data using five Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
SOC 2 is essential for companies handling sensitive customer information such as SaaS providers, cloud platforms, and financial institutions. Certification assures clients that their data is protected from breaches, unauthorized access, and operational failures.
SOC2 – Because ‘trust me bro’ doesn’t work with auditors.
SOC 2 Trust Services Criteria (TSC)
SOC 2 is built on five key principles:
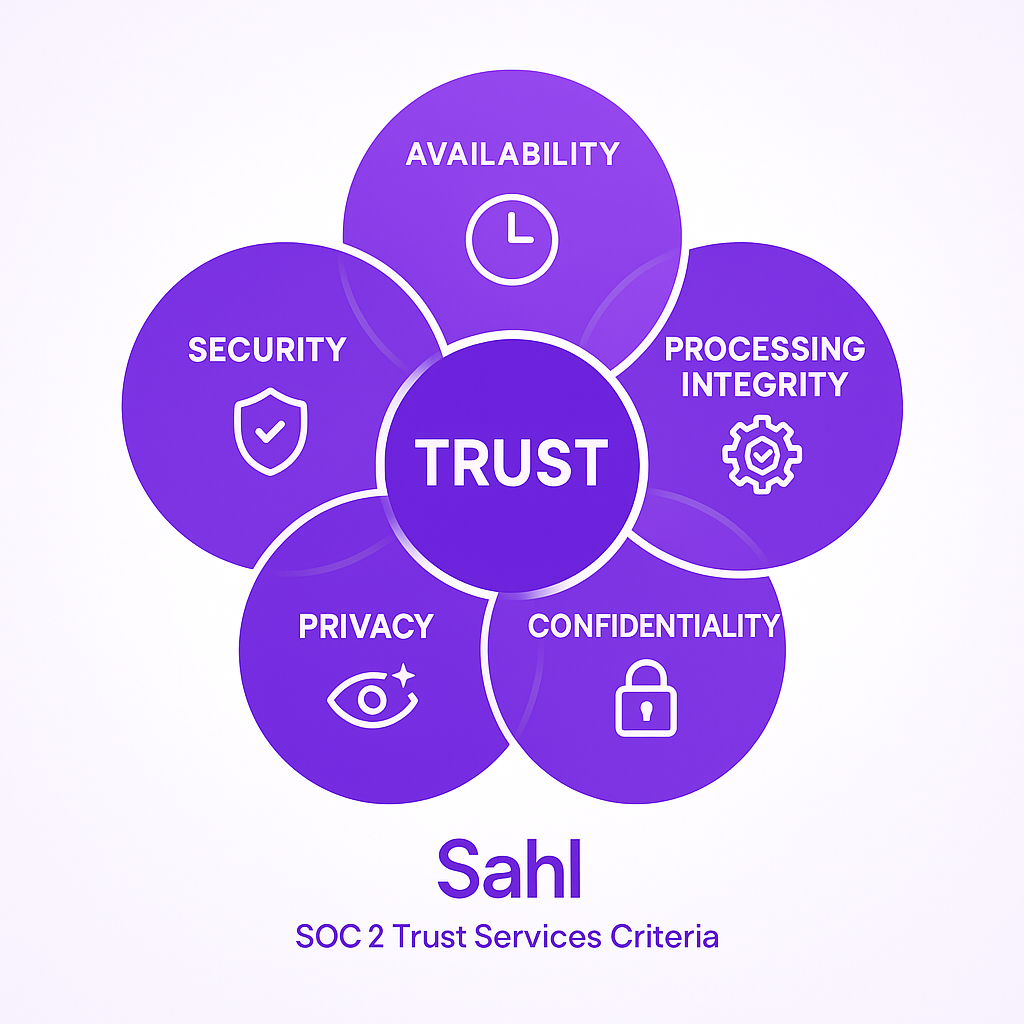
Security : Prevent unauthorized access, breaches, and cyberattacks.
Availability : Keep systems reliable and operational.
Processing Integrity : Ensure accurate, secure, and error-free processing.
Confidentiality : Protect sensitive business and customer data.
Privacy : Safeguard personal information according to regulations.
Sahl enables continuous monitoring, enforcement, and validation of these principles, ensuring readiness for audits and maintaining a strong security posture.
Automating SOC 2 compliance with Sahl
Achieving SOC 2 compliance requires ongoing monitoring, evidence gathering, and risk management. Sahl simplifies this process by:
- Streamlining compliance : Automating evidence collection, risk assessments, and monitoring for continuous readiness.
- Seamless integration : Connecting with your existing security tools to enforce SOC 2 controls.
- Reducing manual work : Tracking trust services criteria automatically to save time and resources.
Sahl’s Approach to Seamless Compliance
With real-time monitoring, automated compliance checks, and guided remediation, SAHL reduces risks and closes security gaps.
We support both:
- SOC 2 Type I – Point-in-time assessment of controls and implementation.
- SOC 2 Type II – Ongoing evaluation of control effectiveness over 3–12 months.
By combining automation with expert guidance, SAHL ensures compliance without disrupting daily operations.
SOC 2 Type I vs. SOC 2 Type II
| Aspect | SOC 2 Type I | SOC 2 Type II |
|---|---|---|
| Focus | Controls are designed appropriately | Controls are designed and operating effectively |
| Timeline | Point-in-time (snapshot on a specific date) | Continuous period (3–12 months) |
| Speed to Achieve | Faster (days) | Longer (months) |
| Audit Evidence | Policies, procedures, configurations at a single point | Logs, monitoring data, incidents, tickets, evidence over time |
| Trust Level | Basic assurance | High assurance – trusted by enterprises & regulators |
| Use Case | Early-stage companies proving readiness | Mature orgs showing consistent compliance |
| Output Report | Confirms design of controls | Confirms design + consistent effectiveness of controls |
Want to see how Sahl's Compliance Automation platform can make SOC 2 easy?
Still have some questions?
1. Who needs SOC 2 compliance?
Any business handling customer data, especially SaaS companies, cloud providers, and financial services benefits from SOC 2 compliance. Many enterprise clients require it before signing contracts.
2. How long does SOC 2 compliance take with Sahl?
Timelines vary, but with Sahl’s automation, businesses typically shorten the process compared to traditional methods, often completing it in under a year.
3. What is the main difference between SOC 2 Type I and Type II?
Type I checks your controls at one point in time, while Type II verifies their effectiveness over several months.
4. What happens if you fail a SOC 2 audit?
Failure can lead to lost contracts, reputational damage, and security vulnerabilities. Sahl helps remediate gaps before reapplying.
5. How does SOC 2 compliance boost trust?
It shows customers that your business takes security seriously, protecting their data according to strict, industry-recognized standards.

