SAMA Cybersecurity Framework Checklist: A Complete Guide for Financial Institutions in 2025

In 2025, the landscape of cybersecurity in the financial sector has evolved dramatically. With increasing digitization, cloud adoption, and fintech integrations, Saudi Arabia’s financial institutions face unprecedented cyber threats. The SAMA Cybersecurity Framework , designed by the Saudi Arabian Monetary Authority , continues to be the backbone of cybersecurity governance and compliance for banks, insurance companies, and fintech firms.
However, compliance isn’t just about meeting regulatory requirements , it’s about establishing trust, resilience, and operational integrity. To simplify the implementation process, financial institutions rely on the sama cybersecurity framework checklist, a practical guide that ensures every domain of cybersecurity is assessed, implemented, and continuously monitored.
This detailed guide provides a 2025-ready perspective on how to understand, implement, and maintain compliance with the SAMA Cybersecurity Framework.
What Is the SAMA Cybersecurity Framework?
The SAMA Cybersecurity Framework is a comprehensive structure developed to unify cybersecurity standards across Saudi Arabia’s financial sector. It ensures that all regulated entities, including banks, insurance firms, and fintechs, follow a consistent approach to managing cybersecurity risks.
The framework defines policies, controls, and governance mechanisms to protect digital assets, customer data, and the integrity of financial transactions. It aligns with global standards such as NIST, ISO 27001, and COBIT while adding regulatory expectations specific to Saudi Arabia’s financial ecosystem.
Its primary goal is to strengthen cyber resilience , the ability of financial institutions to anticipate, withstand, and recover from cyber incidents.

Why Is the SAMA Cybersecurity Framework Checklist Essential in 2025?
The sama cybersecurity framework checklist is not just a compliance document , it’s a strategic tool. It helps organizations translate SAMA’s regulatory expectations into actionable items.
Here’s why every financial institution must use it in 2025:
- Regulatory Compliance: SAMA mandates regular cybersecurity assessments; non-compliance can lead to regulatory penalties.
- Operational Resilience: The checklist ensures business continuity during cyber incidents.
- Risk Reduction: By addressing vulnerabilities, institutions can prevent financial and reputational losses.
- Standardization: It harmonizes cybersecurity governance across departments and subsidiaries.
- Audit Readiness: Provides documentation and evidence needed for audits and assessments.
How Does the SAMA Cybersecurity Framework Checklist Work?
The sama cybersecurity framework checklist serves as a structured assessment tool divided into several key domains. Each domain contains specific objectives and control requirements to ensure compliance.
Institutions can use this checklist to:
- Evaluate current cybersecurity maturity against SAMA’s expectations.
- Identify gaps and prioritize remediation actions.
- Develop a roadmap for achieving the desired maturity level.
- Prepare for audits by maintaining documentation and evidence of compliance activities.
Let’s break down the major components of this checklist.
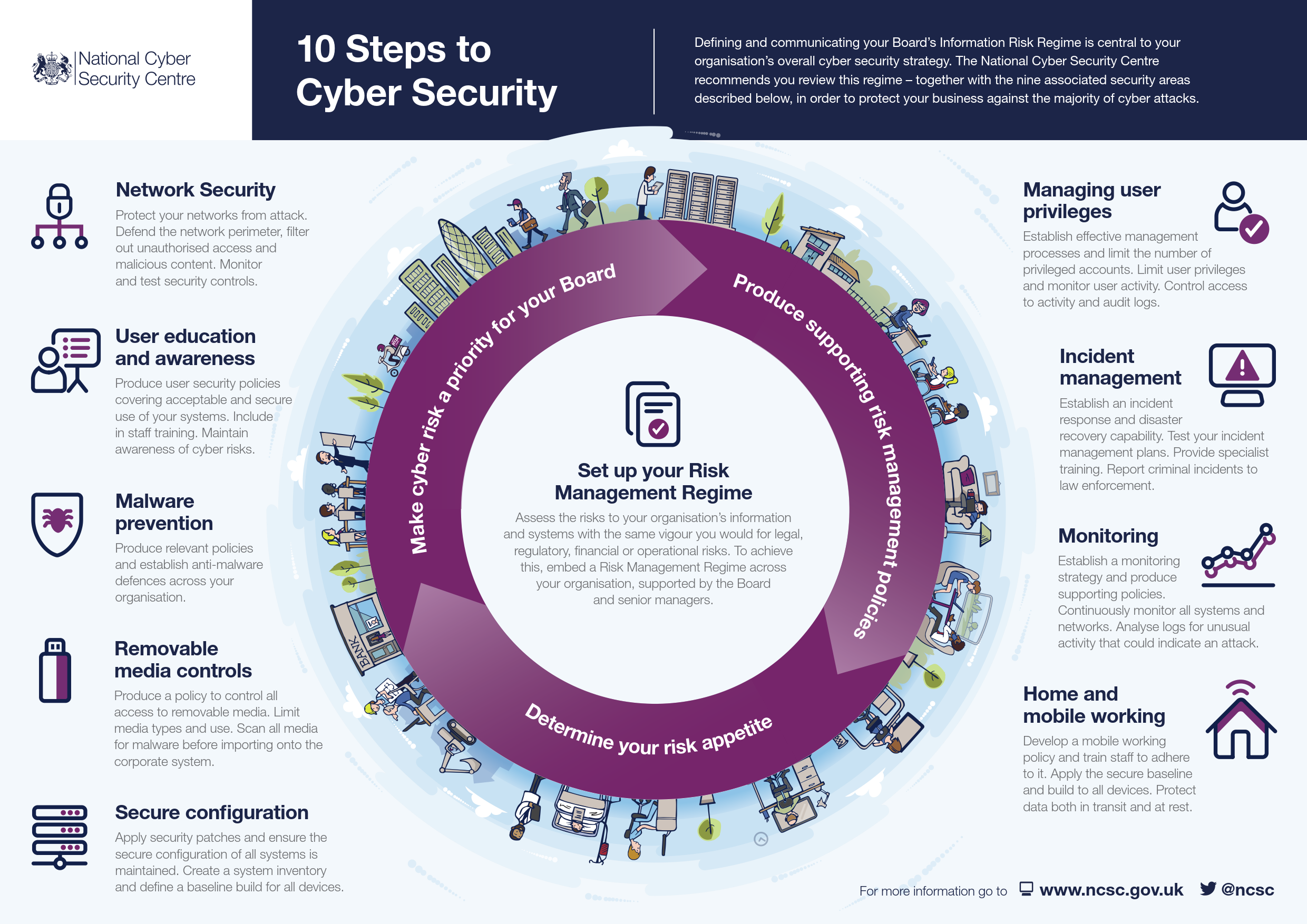
Governance and Leadership , Who Owns Cybersecurity in Your Organization?
A successful cybersecurity program begins with governance. This domain ensures that leadership takes accountability for cybersecurity risk.
Key Actions in the Checklist:
- Establish a Cybersecurity Steering Committee with executive oversight.
- Define roles and responsibilities for cybersecurity management.
- Develop and approve a Cybersecurity Policy aligned with SAMA guidelines.
- Integrate cybersecurity objectives into corporate governance and board reporting.
- Conduct periodic board-level reviews of cybersecurity risks and metrics.
Leadership engagement is crucial, SAMA expects board members to actively monitor cybersecurity performance and ensure adequate resources are allocated.
Risk Management , How Do You Assess and Control Cyber Risks?
The heart of the sama cybersecurity framework checklist lies in identifying and mitigating risks.
Core Steps:
- Create a risk management framework tailored to your organization’s operations.
- Maintain a comprehensive risk register documenting threats, vulnerabilities, and controls.
- Conduct periodic risk assessments using quantitative and qualitative methods.
- Define risk appetite and tolerance levels approved by senior management.
- Ensure that all new projects undergo cyber risk assessments during design and implementation.
Effective risk management aligns cybersecurity investments with business priorities, reducing exposure while supporting innovation.
Asset Management , Do You Know What You’re Protecting?
You can’t protect what you don’t know. Asset management is the foundation of effective cybersecurity governance.
Checklist Inclusions:
- Maintain an up-to-date asset inventory of all hardware, software, and data assets.
- Classify assets based on confidentiality, integrity, and availability.
- Assign ownership and accountability for each critical asset.
- Ensure automated discovery tools are used for continuous asset visibility.
This step ensures that critical systems are identified and prioritized for protection, forming the base for all other cybersecurity controls.
Access Control , Who Has Access to What?
The SAMA Cybersecurity Framework emphasizes strong identity and access management (IAM). Unauthorized access remains one of the leading causes of data breaches.
Checklist Components:
- Implement least privilege access for all users.
- Enforce multi-factor authentication (MFA) across systems.
- Regularly review and update access rights based on role changes.
- Use Privileged Access Management (PAM) for sensitive accounts.
- Automate access provisioning and deprovisioning processes.
A mature access control system protects sensitive data and ensures compliance with sama cybersecurity compliance requirements.
Data Protection , How Secure Is Your Sensitive Information?
Data is the lifeblood of any financial institution, and protecting it is central to the sama cybersecurity framework checklist.
Key Activities:
- Classify data based on sensitivity and apply encryption policies.
- Encrypt data at rest and in transit.
- Implement data loss prevention (DLP) tools.
- Establish a secure data disposal policy.
- Regularly test backup and recovery processes.
The goal is to prevent unauthorized disclosure, modification, or loss of data , a fundamental requirement in cyber security sama guidelines.
Security Operations , How Prepared Are You for Daily Threats?
The sama cybersecurity framework pdf outlines stringent requirements for operational security.
Operational Controls:
- Deploy a Security Information and Event Management (SIEM) system.
- Establish 24/7 monitoring via a Security Operations Center (SOC).
- Use threat intelligence feeds for proactive defense.
- Implement vulnerability scanning and patch management programs.
- Create incident escalation protocols for rapid response.
These measures help identify and respond to incidents in real-time, enhancing resilience against cyberattacks.
Incident Response and Recovery , Are You Ready for a Breach?
Even the best defenses can be breached. The sama cybersecurity framework checklist includes detailed incident response procedures.
Response Essentials:
- Develop a formal Incident Response Plan (IRP) approved by management.
- Conduct incident simulation exercises and tabletop tests annually.
- Maintain forensic readiness for evidence preservation.
- Create clear communication protocols for internal and external stakeholders.
- Integrate lessons learned into continuous improvement plans.
A mature incident response process ensures minimal downtime and preserves customer confidence during crises.
Third-Party Management , Are Your Vendors Compliant?
Financial institutions rely heavily on third-party service providers , from cloud hosting to payment gateways.
Checklist Items:
- Maintain an inventory of all third-party vendors with access to critical data.
- Conduct due diligence assessments before onboarding.
- Include cybersecurity clauses in contracts.
- Require vendors to align with the SAMA cybersecurity compliance framework.
- Continuously monitor vendor performance and conduct audits.
Vendor risk is one of the most overlooked threats; enforcing SAMA’s requirements on third parties is essential.
Business Continuity and Disaster Recovery , Can You Survive a Major Outage?
Resilience goes beyond prevention; it’s about recovery.
Key Requirements:
- Develop a Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP).
- Identify critical business functions and dependencies.
- Conduct annual BCP/DRP tests simulating real-world cyber incidents.
- Ensure redundant systems and off-site backups exist for essential services.
SAMA expects institutions to maintain service availability, even under severe cyber disruptions.
Business Continuity and Disaster Recovery , Can You Survive a Major Outage?
Cybersecurity isn’t static. Threats evolve, and compliance expectations rise each year.
Continuous Improvement Practices:
- Conduct annual reviews of cybersecurity policies and controls.
- Update the sama cybersecurity framework checklist based on new threats or technologies.
- Implement a cybersecurity awareness program for employees.
- Benchmark performance against industry peers.
Continuous improvement ensures that your organization remains adaptive and compliant as technology and regulations change.
How to Prepare for SAMA Cybersecurity Audits
To demonstrate compliance, financial institutions must provide evidence of adherence to SAMA’s controls.
Preparation Tips:
- Maintain comprehensive documentation for each control domain.
- Keep records of risk assessments, policies, incident logs, and reports.
- Perform internal audits before official inspections.
- Leverage automation to track compliance status in real time.
- Assign control owners responsible for remediation and reporting.
By following the sama cybersecurity framework checklist, organizations can confidently face SAMA audits without last-minute stress.
The Future of Cyber Security SAMA in 2025 and Beyond
In 2025, cybersecurity in Saudi Arabia continues to evolve. The SAMA cybersecurity framework is expected to expand with enhanced requirements for cloud computing, AI-driven monitoring, and digital banking.
Financial institutions that integrate cybersecurity governance into their culture , not just their technology stack , will gain a significant edge. The checklist will remain the foundation for maintaining resilience, trust, and Soc2 compliance.
Conclusion
The sama cybersecurity framework checklist is more than a compliance tool , it’s a strategic asset that defines how financial institutions in Saudi Arabia approach risk, governance, and technology in 2025 with the help of Sahl.
By rigorously applying this checklist, organizations can:
- Strengthen their cyber resilience
- Ensure regulatory compliance
- Build trust with customers and stakeholders
- Position themselves as leaders in secure digital finance
As cyber threats grow more complex, the only way forward is proactive governance backed by a structured framework , and SAMA’s cybersecurity standards offer just that.
FAQs
1. What is the main purpose of the SAMA Cybersecurity Framework?
The main goal is to establish a unified standard for cybersecurity across Saudi Arabia’s financial institutions, ensuring consistent protection of information and services.
2. Who must comply with the SAMA Cybersecurity Framework?
All financial institutions regulated by SAMA , including banks, insurance companies, and fintech providers , must adhere to the framework.
3. What does the sama cybersecurity framework checklist include?
It covers governance, risk management, access control, incident response, third-party management, and business continuity among other domains.
4. How often should institutions review their cybersecurity framework compliance?
Organizations should review compliance at least annually, or whenever major technological or regulatory changes occur.5. Is there a sama cybersecurity framework pdf available for download?
Yes, institutions can access the official PDF from SAMA’s regulatory portal, which includes detailed requirements and control guidelines.

