Essential Eight Cybersecurity
When you use digital systems, you expect security to be strong and consistent. Behind the scenes, one framework helps organizations achieve that: the Essential Eight.
What is the Essential Eight?
The Essential Eight is a set of baseline cybersecurity strategies developed by the Australian Cyber Security Centre (ACSC) to help organizations mitigate cyber threats. Instead of being a broad guideline, it provides practical and prioritized security measures that protect against the majority of common attacks.
Think of the Essential Eight as a cyber resilience playbook, helping businesses safeguard systems, reduce vulnerabilities, and strengthen defenses against cybercrime.
For more info, see the ACSC overview: Essential Eight Maturity Model.

Why Essential Eight Cybersecurity Compliance Feels Complex
Organizations often find Essential Eight compliance challenging because it requires:
• Assessing current security maturity across multiple domains
• Implementing technical safeguards such as patching, whitelisting, and backups across all systems
• Managing user access tightly with multifactor authentication and least privilege
• Continuously monitoring, updating, and testing controls to maintain resilience
• Demonstrating maturity levels during external audits or risk assessments
It is not just about deploying security tools, it is about embedding cybersecurity into day to day IT operations and governance.
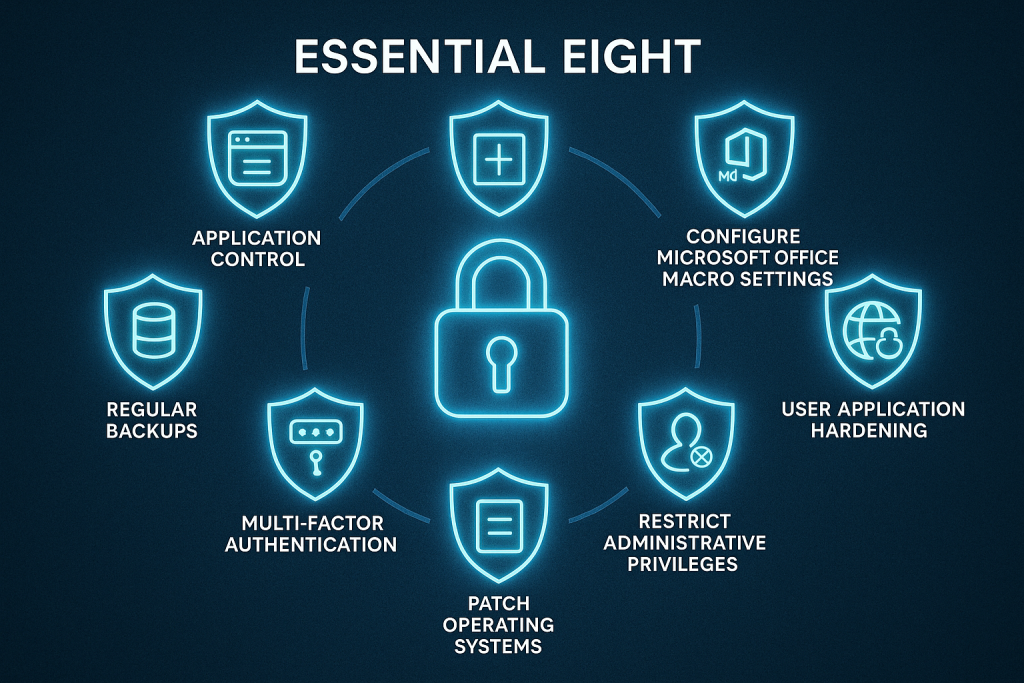
Core Strategies of the Essential Eight
The framework is structured around eight mitigation strategies:
- Application Control Prevent unauthorized applications from running
- Patch Applications Regularly update and patch software vulnerabilities
- Configure Microsoft Office Macro Settings Restrict macros to reduce malware risks
- User Application Hardening Harden browsers and applications to block malicious content
- Restrict Administrative Privileges Limit privileged access and monitor admin activity
- Patch Operating Systems Keep operating systems fully updated and supported
- Multi Factor Authentication (MFA) Require MFA for accounts, especially privileged ones
- Regular Backups Ensure data is backed up, tested, and recoverable
Risk Based Thinking in the Essential Eight
The Essential Eight uses a maturity model approach, recognizing that not all organizations are at the same security level. It requires businesses to evaluate:
• Threats: which attacks are most likely against your systems
• Vulnerabilities: which gaps could attackers exploit
• Impact: what damage an incident could cause to operations and data
Instead of one size fits all, the maturity model has three levels (Maturity 1 to 3) guiding organizations to progressively strengthen their defenses. This approach embeds risk based thinking so organizations identify their most critical risks and address them systematically.
Benefits of Essential Eight Cybersecurity Compliance
Achieving Essential Eight compliance demonstrates to regulators, customers, and partners that cybersecurity is taken seriously. Benefits include:
• Reduced cyber risk by blocking common attack vectors
• Improved resilience to ransomware, phishing, and data breaches
• Greater customer trust by showing proactive security management
• Operational continuity through robust backups and recovery plans
• Regulatory alignment with government and industry requirements
Internally, it strengthens IT culture by clarifying roles, standardizing security practices, and improving collaboration between IT, compliance, and business teams.
How Sahl Simplifies Essential Eight Cybersecurity Compliance
With Sahl’s Compliance Automation platform, Essential Eight compliance becomes faster and less resource heavy. The platform can:
• Automate maturity assessments to identify gaps
• Track and log patch management across applications and operating systems
• Enforce and monitor MFA adoption
• Provide audit ready evidence for each Essential Eight control
• Streamline reporting to keep stakeholders and auditors aligned
This allows businesses to focus on growth and service delivery while maintaining a robust cybersecurity baseline.
FAQs
- Who needs the Essential Eight?
Any organization seeking to protect itself from common cyber threats, especially those in government supply chains or critical industries. - Is the Essential Eight mandatory?
Not always, but for Australian government agencies and contractors it is increasingly required. Many private businesses adopt it as best practice. - Does the Essential Eight apply outside Australia?
Yes. While designed by the ACSC, its strategies are universal cybersecurity best practices. - How long does it take to achieve compliance?
It depends on your current maturity. With automation and strong governance, businesses accelerate readiness significantly. - Does it work for small businesses?
Yes. The maturity model makes it scalable from small companies to large enterprises. - How often should maturity be assessed?
At least annually, or after significant IT or environmental changes.

