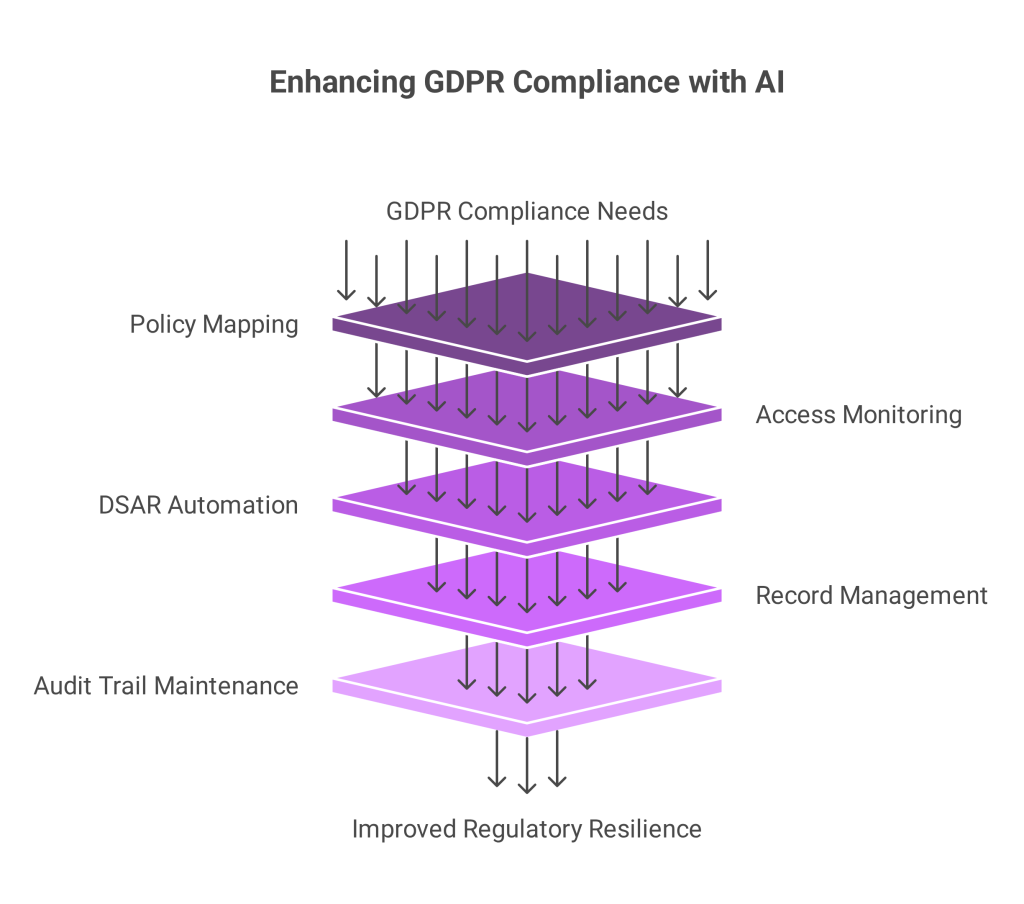
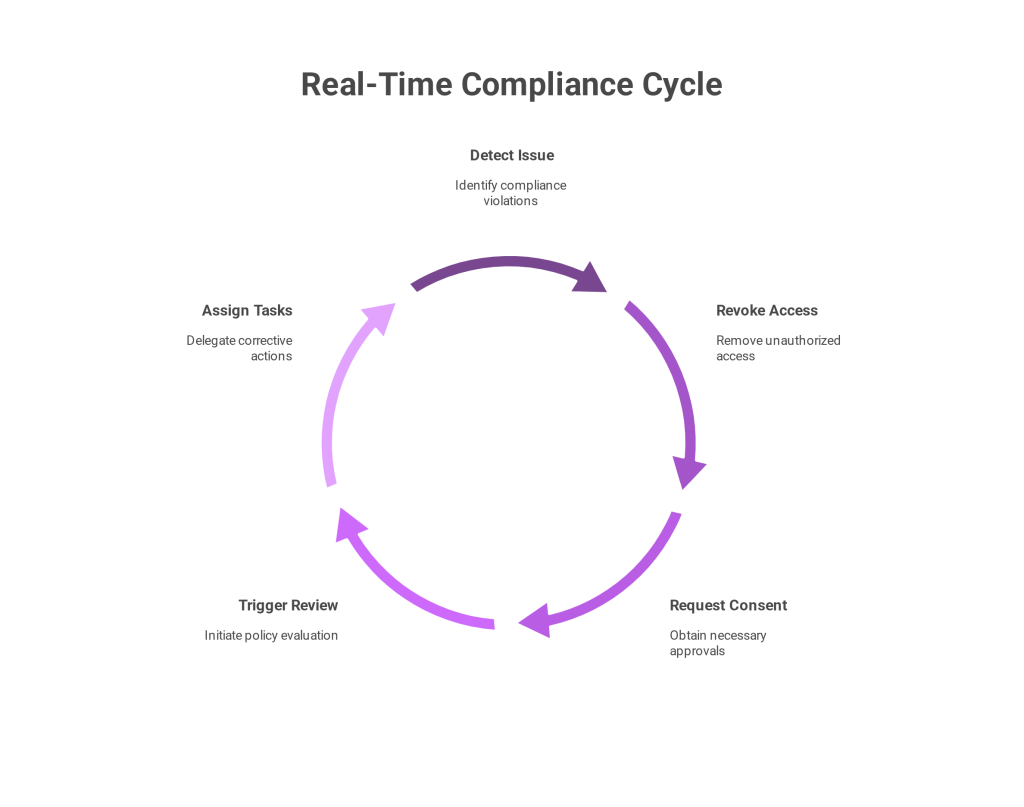
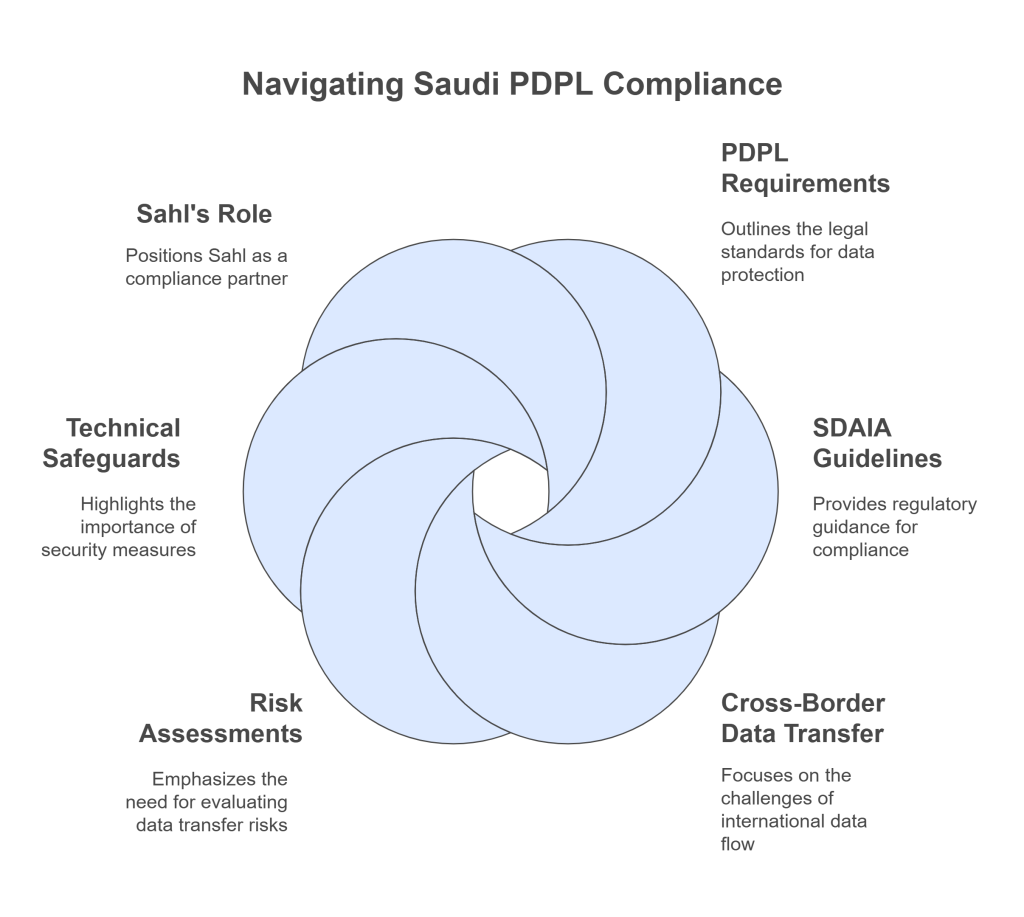
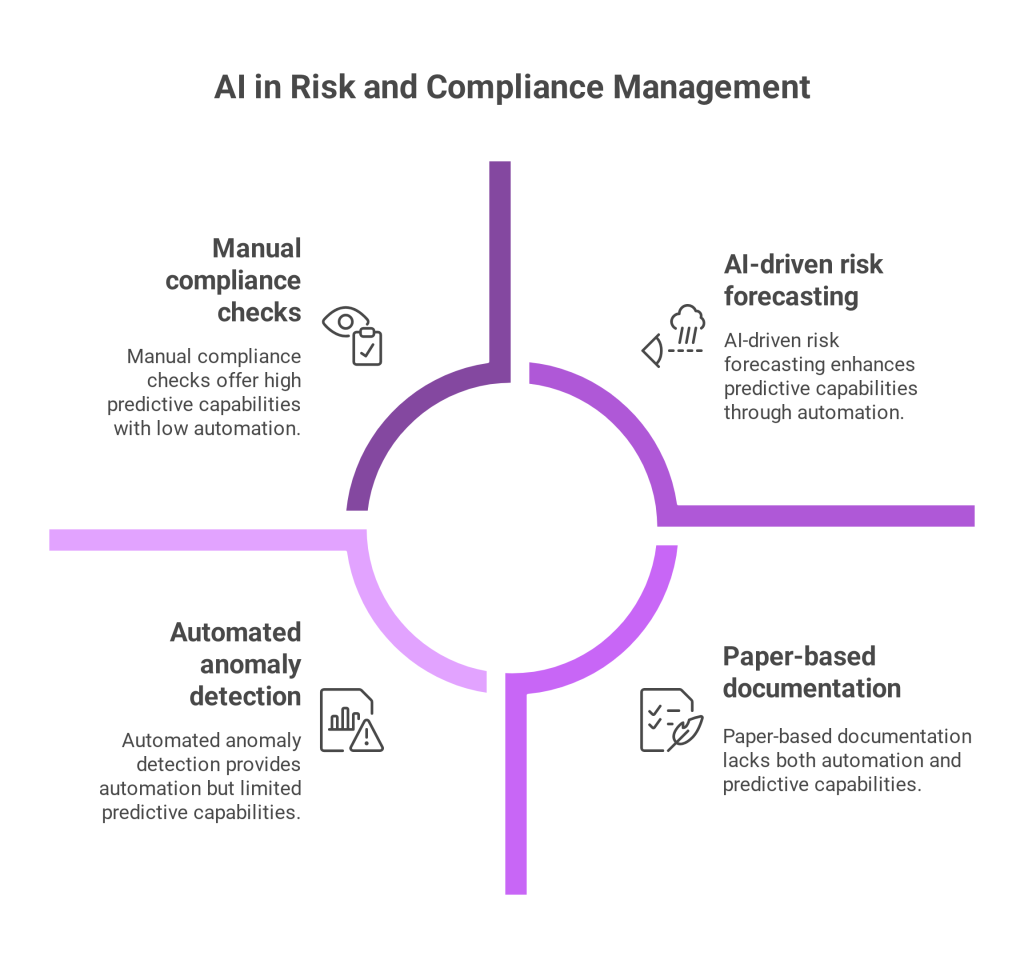
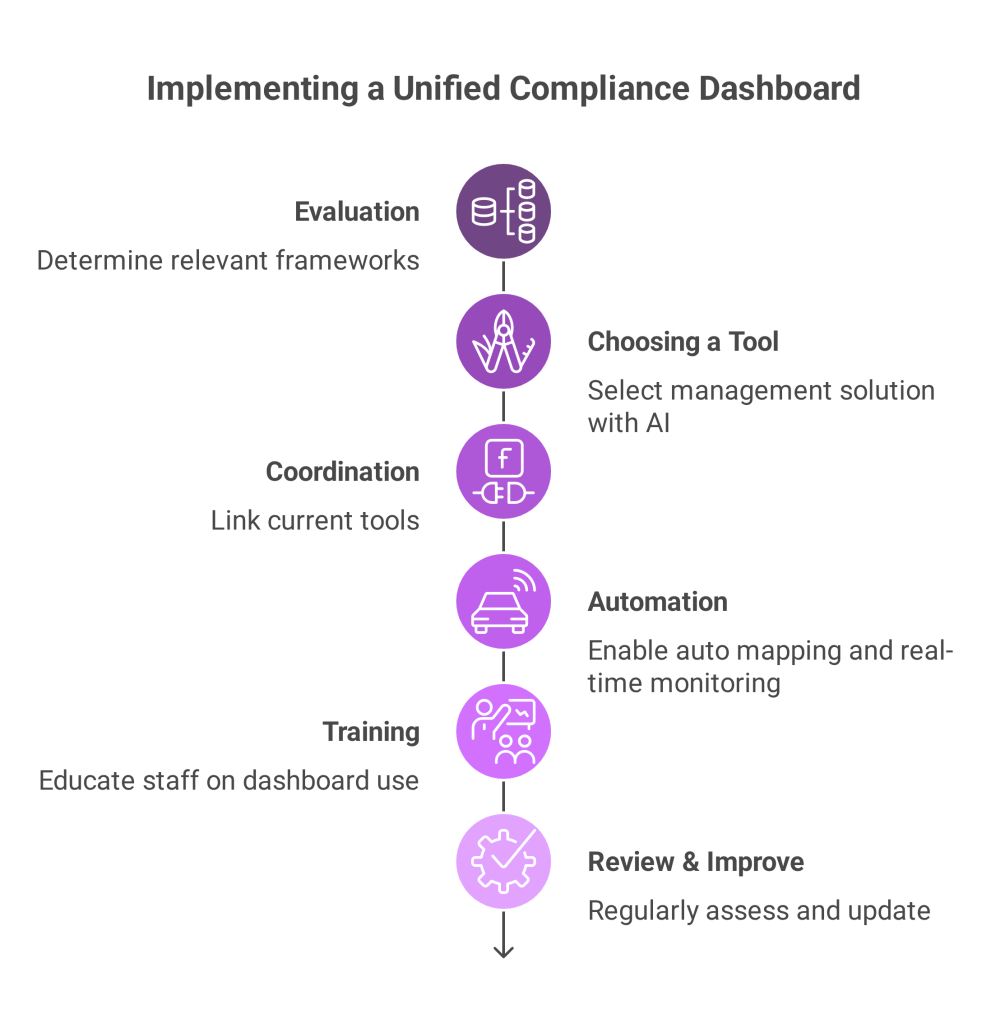
In today’s interconnected digital economy, businesses operating in or with Saudi Arabia cannot afford to overlook the legal obligations surrounding cross-border data transfers under PDPL. The Saudi PDPL is now fully enforceable. Organizations must take a meticulous approach to compliance, or risk severe penalties.
For companies seeking a more innovative way to navigate these regulations, Sahl stands at the forefront of compliance automation, empowering businesses to ensure lawful, secure, and efficient cross-border data transfers under PDPL.
Understanding PDPL Data Transfers and Cross-Border Rules
The PDPL applies to any organization processing the personal data of individuals residing in the Kingdom, regardless of whether the business is located within or outside Saudi Arabia. It imposes detailed conditions on how and when data can be transferred outside the country, especially in the absence of an adequacy decision by the Saudi Data & Artificial Intelligence Authority (SDAIA).
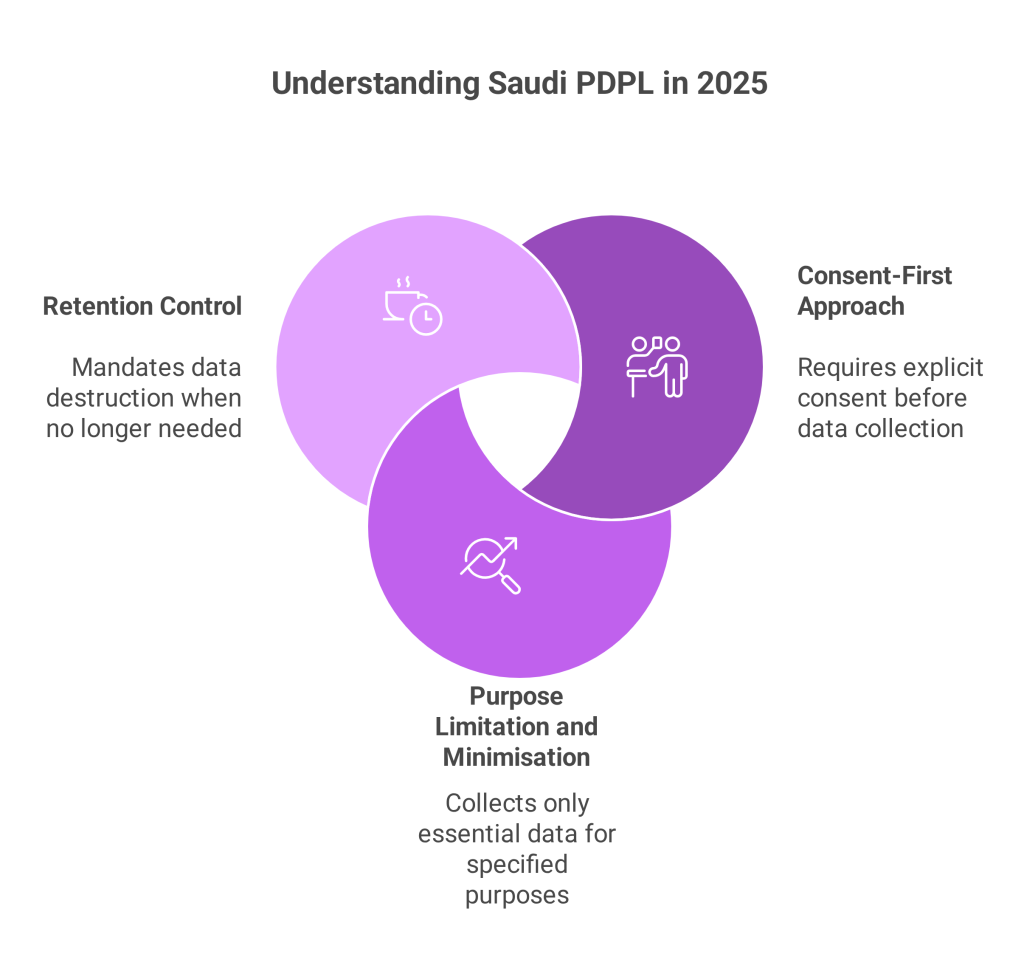
Cross-border data transfers under PDPL must not compromise national security or Saudi Arabia’s vital interests and must always be limited to the minimum data necessary for a legitimate, authorized purpose. Organizations must map each data transfer to a lawful basis, whether it serves a data subject, fulfills a contract, or enables central operations.
Legal Requirements for PDPL Data Transfers: Consent, Purpose, Minimization
To begin with, organizations must first identify when and how personal data is collected and ensure individuals are informed that their data may be transferred abroad. Explicit consent must be obtained, documented, and tied to a clearly defined purpose. However, PDPL requires more than just consent, transfers must still meet legal standards for necessity, proportionality, and authorized business function.
To maintain compliance, companies must:
- Inform data subjects about the transfer’s purpose, destination, and scope
- Document consent in a verifiable manner
- Maintain records of processing activities that detail the legal basis for the transfer
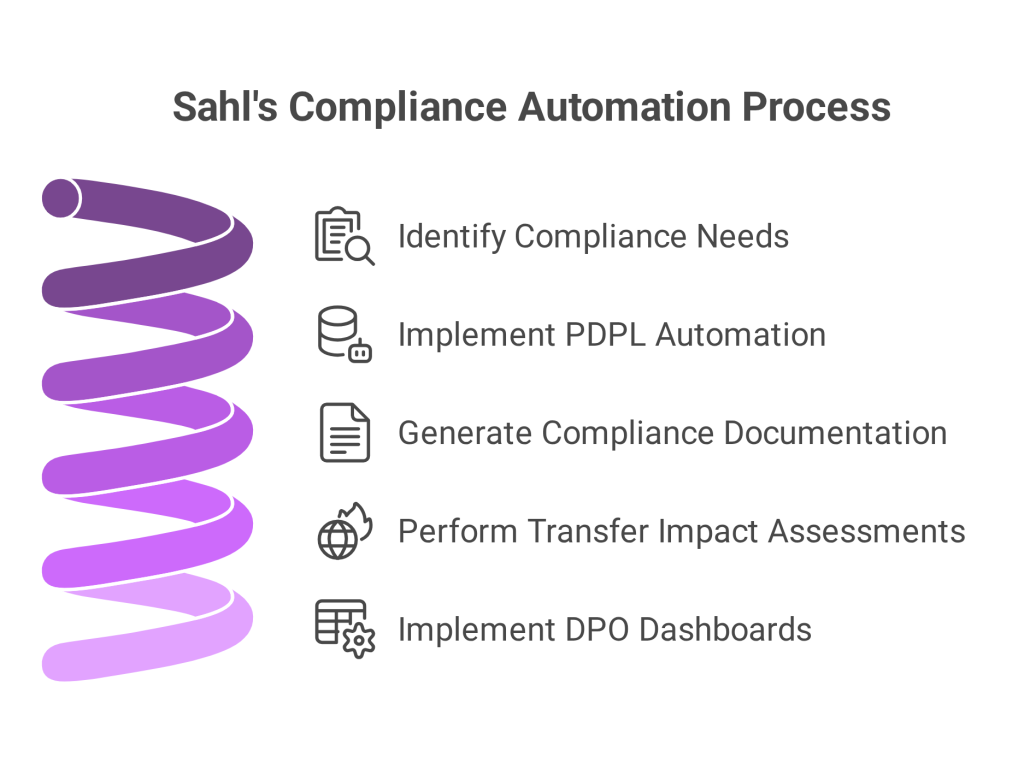
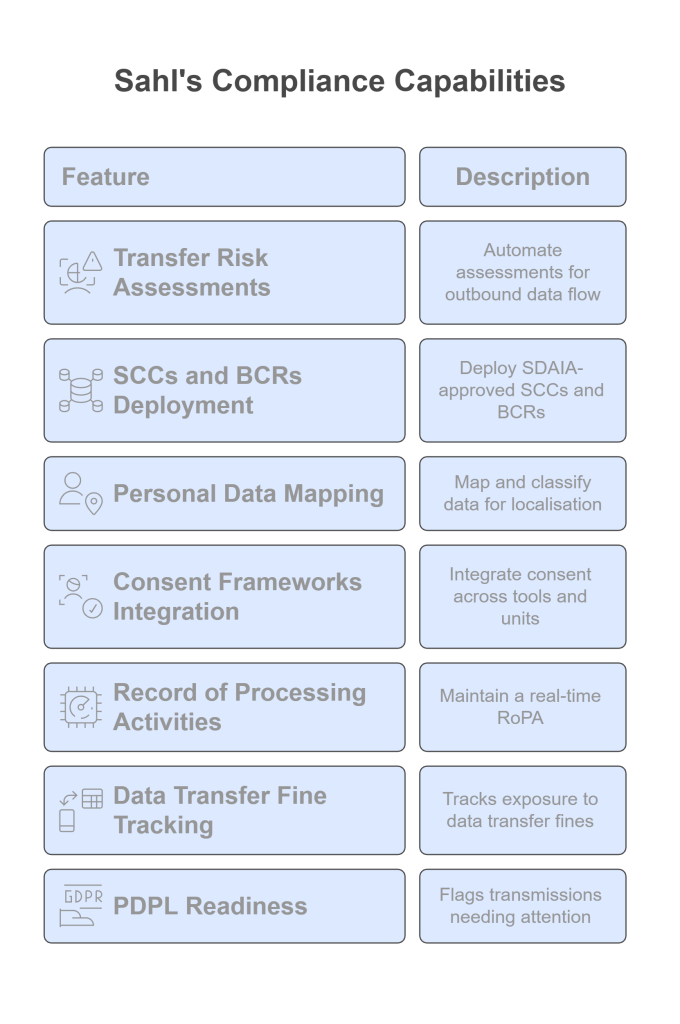
Furthermore, organizations must document every transfer decision to ensure traceability and accountability under PDPL. By automating the complexities of cross-border data transfers PDPL compliance demands, Sahl helps businesses avoid manual errors and regulatory oversights. The platform streamlines consent workflows, data mapping, and transfer justifications, ensuring traceability and legal readiness at every step.
Appropriate Safeguards for International PDPL Transfers
If the receiving country has not yet been deemed to offer adequate data protection, the PDPL requires that “appropriate safeguards” be implemented. These include:
- Standard Contractual Clauses (SCCs) issued by SDAIA
- Binding Corporate Rules (BCRs) for multinational groups
- Certificates of accreditation or legal undertakings
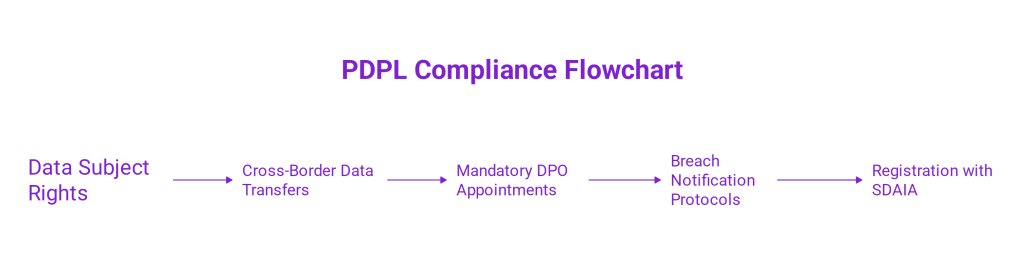
Each safeguard must guarantee enforceable rights for data subjects and clearly outline the roles, responsibilities, and breach notification protocols between controllers and processors. Organizations must also conduct a Transfer Impact Assessment (TIA) to evaluate risks, data types involved, safeguards in place, and potential harm to individuals.
With Sahl’s compliance platform, businesses can integrate approved SCCs, document BCRs, and automate TIAs, streamlining cross-border data transfers under PDPL across jurisdictions.
Sector-Based Compliance for PDPL Data Transfers in Saudi Arabia
Additional approvals from sector-specific regulators, such as the Saudi Central Bank, may be required in sensitive sectors like finance or healthcare. Sensitive data, including health, genetic, biometric, and credit data, demands heightened security measures and prior authorisation.
Controllers must:
- Limit access to authorized personnel
- Encrypt data in transit and at rest
- Implement continuous monitoring
SDAIA has also introduced a public register for controllers and a mandatory DPO (Data Protection Officer) requirement for high-risk data processing activities. Organizations must maintain privacy policies, destruction protocols, and records of processing aligned with PDPL standards.
Sahl simplifies these operational burdens with centralized dashboards that help businesses stay aligned with SDAIA’s latest legal requirements and security best practices.
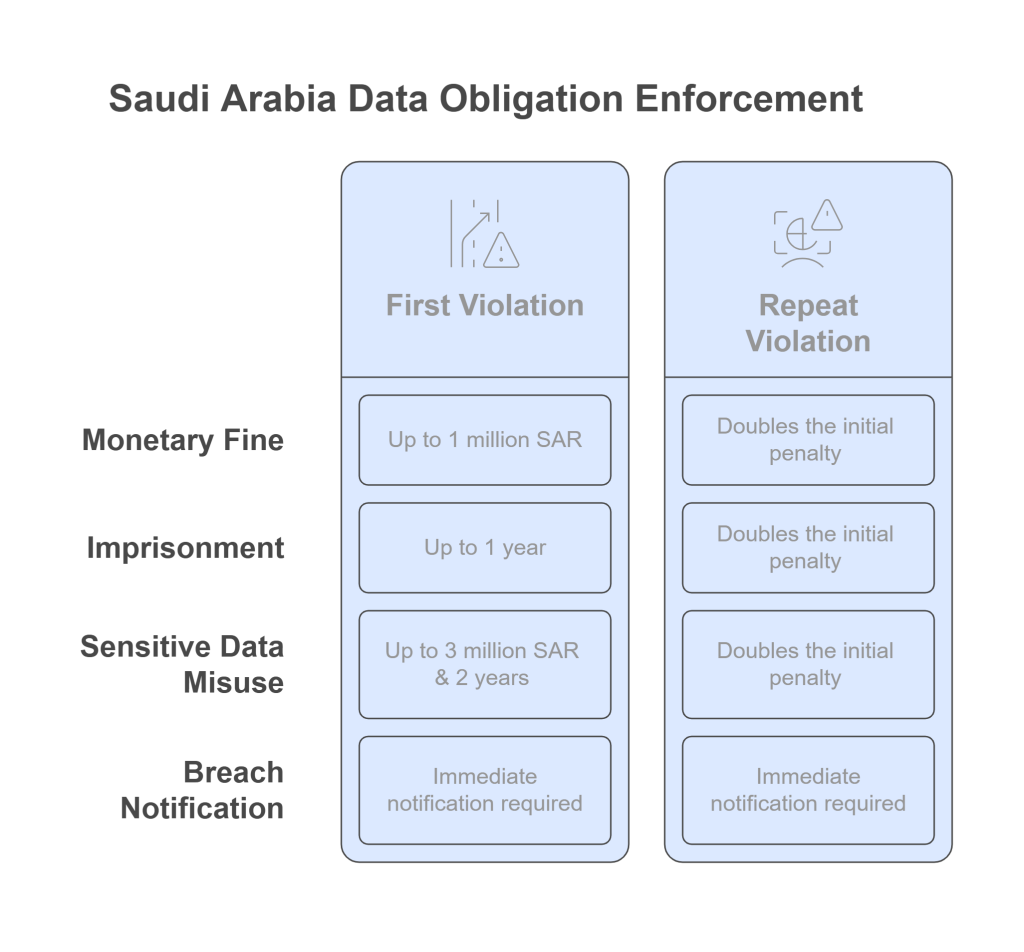
What Happens If You Violate PDPL Data Transfer Laws?
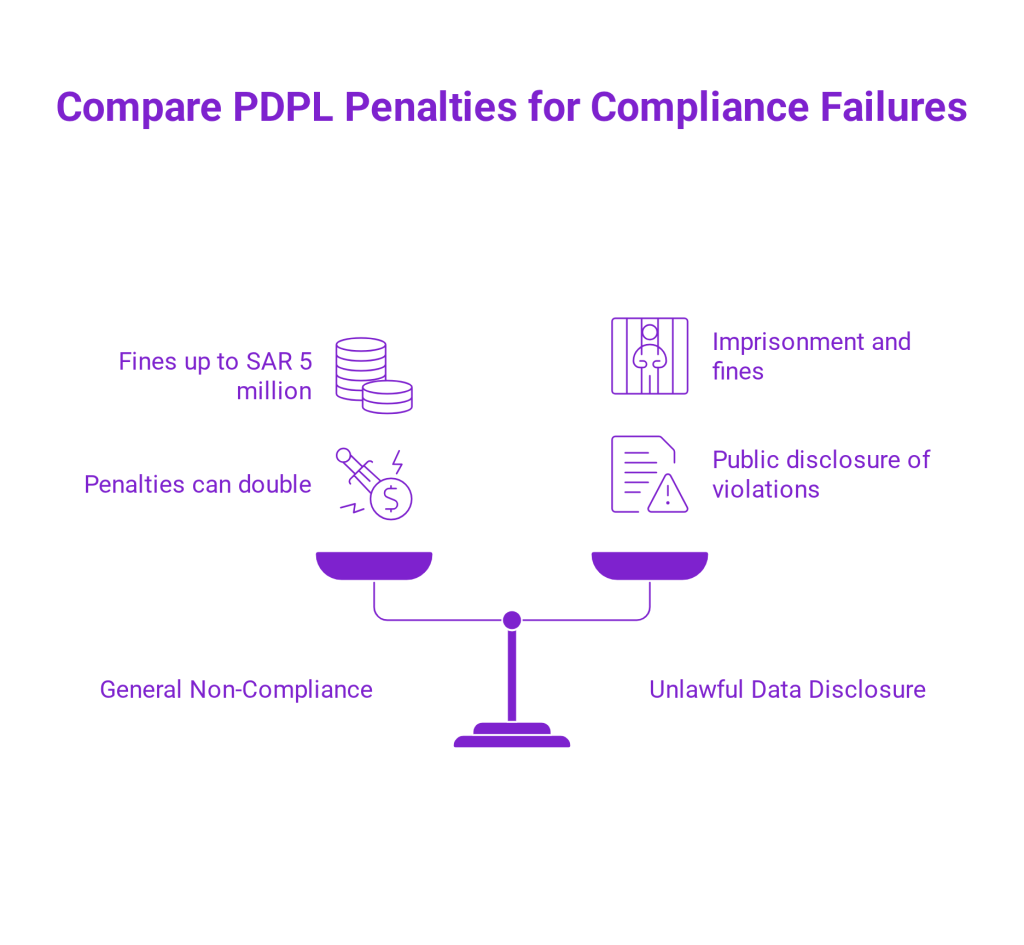
Failure to comply with cross-border data transfers PDPL requirements may result in:
- Criminal prosecution
- Fines up to SAR 5 million
- Reputational damage
- Regulatory investigations triggered by complaints or audits
Consequently, non-compliance can lead to steep penalties that damage not only finances but also public trust and investor confidence. With enforcement intensifying post-September 2024, companies must act decisively. Proactivity is no longer optional, it is a necessity.
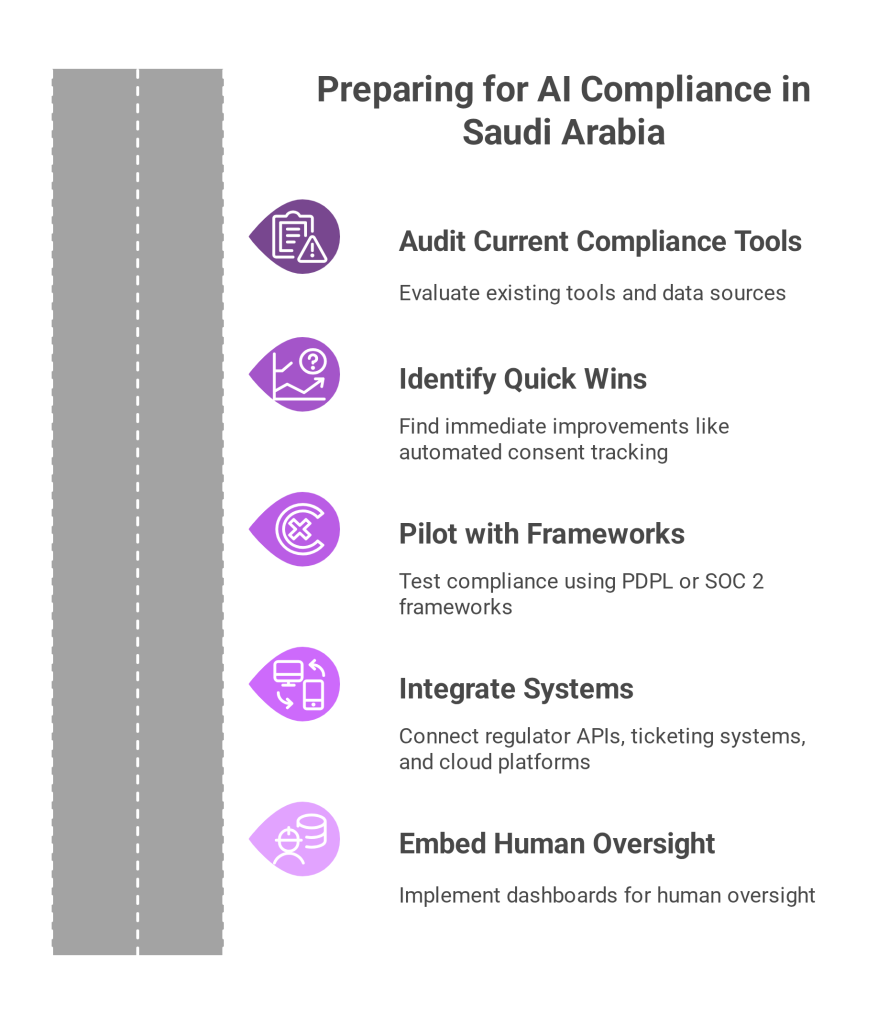
How Sahl Simplifies PDPL Data Transfers with Automation
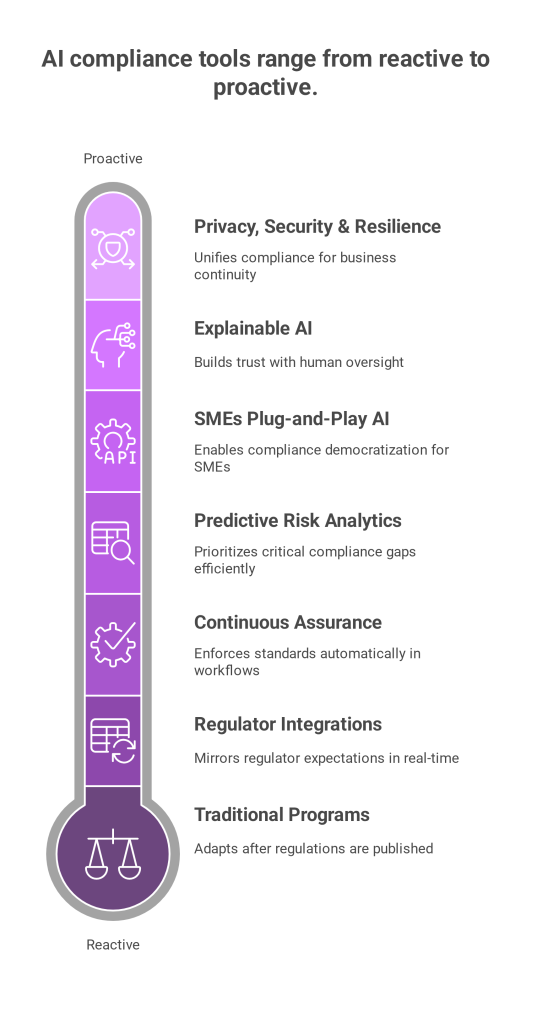
Simply put, manual compliance is no longer viable in a regulatory landscape as complex as Saudi Arabia’s data protection ecosystem.I n contrast, automated platforms reduce the burden significantly by eliminating repetitive tasks, reducing human error, and accelerating audit readiness.
Sahl’s automation-driven platform is purpose-built for PDPL and supports:
- Consent orchestration and documentation
- Automated Transfer Impact Assessments
- Integration of SCCs and BCRs
- Secure workflows for sensitive data
- Continuous compliance monitoring
In short, automation saves time and reduces legal exposure, giving your team the ability to move faster while staying compliant. Sahl’s automation eliminates friction in managing cross-border data transfers PDPL regulations impose, giving your business clarity, speed, and peace of mind.
✅ Ready to protect your data and expand globally, without legal friction?
Explore Sahl’s compliance automation platform today and move forward with clarity and confidence.